CCI Network Overview
The Center for Computational l Innovation (CCI) operates an isolated network environment. This network provide communication between servers inside the center, but no direct connection outside the center.
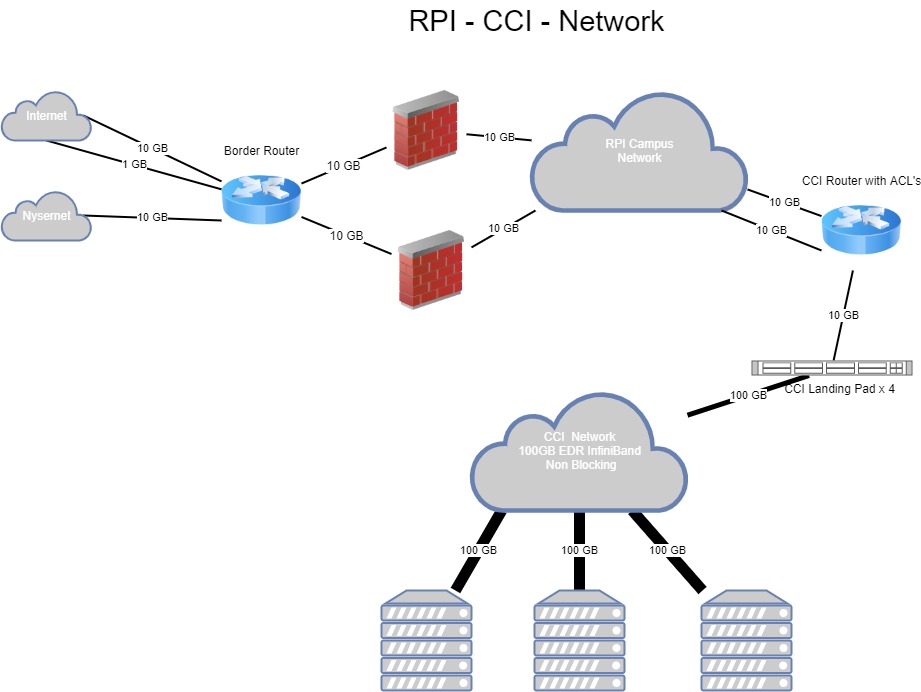
CCI’s upstream access to the Internet flows through RPIs main campus network and is protected by the same edge firewalls. These firewalls limit access to CCI. They only allow access to authorized ports on specific IPs and block all access from known bad IP’s.
The CCI Router limits access from RPI’s main campus network to authorized ports on specific IPs of the CCI edge servers. In general this is the same access as permitted to the Internet. There are additional exceptions to allow traffic from authorized IT scanning, monitoring and management systems.
CCI’s landing pads are the edge systems that clients on the Internet and RPI’s network can connect to. In addition to the landing pads the management servers are also edge systems. Edge systems are dual homed with a network connection on both the CCI Internal and External networks. No traffic is routed from the CCI internal network.
CCI’s landing pad protect themselves using 2 factor authentication and block IPs that fail to login too many times. The only protocol allowed to the landing pads is SSH.
Access to the Internet from CCI’s internal network is via a proxy server and limited to authorized whitelisted sites. Additionally, all DNS requests from CCI systems are filtered by Cisco’s Umbrella DNS security product.
Typical data flow¶
A typical user will use SSH to connect to a CCI landing pad. They will provide a username, two factor code and a password to gain access. They can then use SSH to copy files to or from the CCI filesystem and run software. CCI uses a single, unified filesystem that is available on the landing pads, cluster front ends, and compute nodes.
From this landing pad they can SSH to a cluster front end to run software on compute nodes. The files they previously copied into the file system will be accessible to them on any CCI computer they log into.
Diagram¶
Caveats¶
- For simplicity we will call Internet, Internet2 and NYSERnet; the Internet